Huawei staff installed malicious code on Aust. network report

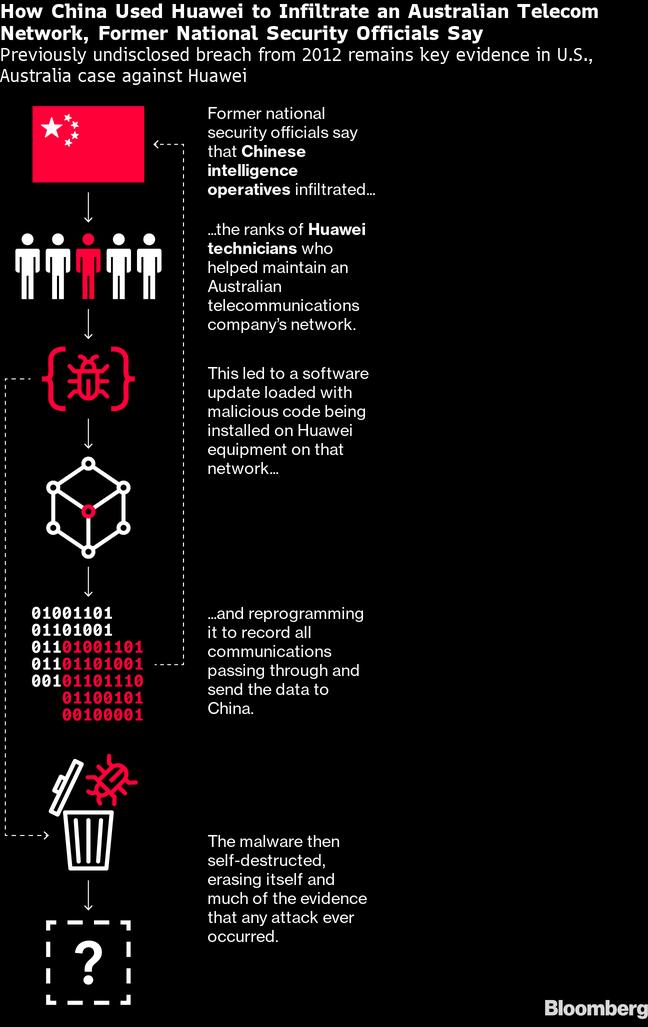
Huawei installed malicious code in an Australian telco network that recorded all communications and transmitted it to China, according to a story by Bloomberg.
The code was embedded in a software patch by Huawei in 2012, most likely in equipment supplied to Optus, Australia's second largest telco, Bloomberg reported.Optus has denied the report.
Who are you? Rumours about Huawei's alleged relationship with the Chinese administration, their security services and the PLA have persisted for years.(Source: Karlis Dambrans on Flickr, CC 2.0)Australian intelligence agencies concluded China's spy services were behind the breach, having infiltrated the Huawei team that had uploaded the software.
They informed counterparts in the US, confirming "suspicions in both countries that China used Huawei equipment as a conduit for espionage," the story said.
Bloomberg said it had substantiated the incident with "nearly two dozen former national security officials," seven of whom had furnished detailed accounts of the event.The software update had contained code that reprogrammed the network equipment to record all data passing through and send it to China. The exploit was short-lived, however, deleting itself after a few days.
Corroborating evidence
Besides seeming to illustrate the threats posed by Huawei equipment, the news is also significant for throwing some light on why the US has been unwavering in its pursuit of Huawei despite the lack of solid evidence.
Washington's hostility to the Chinese vendor long pre-dates the current tensions between the two countries and the gathering tech war. As far back as 2008, the US blocked Huawei's attempt to acquire 3Com's China business.
The news of this 2012 exploit helps fill in the gap in public understanding of how the US and allies came to view Huawei equipment as high-risk.That said, we know nothing of the context of the breach and how much, if anything Huawei leaders knew of it.
Huawei denied the claims as it has on all previous occasions.
But in an emailed statement to reporters it does itself few favors, attacking the story as "unsubstantiated" and lacking credibility for being unreported for so long. Intelligence officers aren't the kind of people who routinely share details of their work, so it is hardly surprising it has remained secret for nearly a decade.
Huawei also declares that its equipment "doesn't have malware," and that its software patches can't be installed if they are tampered with but every bit of software has a workaround.
This latest bit of reporting doesn't convict Huawei of colluding with Beijing authorities, but it does suggest it may be vulnerable to infiltration by Chinese intelligence.
That was the basis of the ban on Huawei by the Australian government in August 2018 the first such formal prohibition on the vendor.
The then-prime minister, Malcolm Turnbull, has said it was not aimed at Huawei specifically, or because of anything the company had done, but about the lack of trust in the Chinese government and its record as a bad actor on cybersecurity.
Turnbull and Australian security officials spent eight months war-gaming scenarios that would allow them to accommodate a Huawei 5G network but concluded they could not prevent it being shut down on Beijing's orders.
In a recent memoir Turnbull wrote that the ban was a "hedge against a future threat, not the identification of a smoking gun, but a loaded one."
Related posts:
Robert Clark, contributing editor, special to Light Reading
- Prev
- Next







